




On September 5th, the National Computer Virus Emergency treatment Center and 360 Company released a survey report on the Northwest Polytechnical University's network attacks by the National Security Agency (TAO) under the National Security Agency (NSA) of the National Security Agency (NSA). More than 40 different types of exclusive network attack weapons continue to attack the stealing of Northwestern Polytechnical University, stealing core technical data such as the school's key network equipment configuration, network management data, and operation and maintenance data.
With the rapid development of global informatization, the entire world is rapidly integrated, and a large number of construction systems that have been built have become the key infrastructure of the country and the government. Many enterprises, organizations, government departments, and institutions are forming and developing their own networks to facilitate sharing and use the network information and resources. The network has become a strong driving force for global economic and social development, and its status is increasingly unavailable. Therefore, the importance of information security is not limited to the country, and the security of information such as government, enterprises, and individuals is equally important.
What are the factors of unsafe network information?
Two major factors affecting network security: nature and human beings. Natural reasons are the leakage of information caused by data storage, computing, transmission and other equipment after encountering extreme weather or other irresistible natural factors. However, there are fewer information leaks caused by natural reasons, and information leakage is more human reason. The cause of the average person can be divided into: network program design bugs and vulnerabilities, back doors and hackers, viruses, or network architectures, and hardware design technology itself has security defects. Programming bugs and vulnerabilities include the TCP/IP protocol defects, security strategy vulnerabilities, and operating system vulnerabilities. As well as the network architecture, hardware performance technology defects caused by the development of hardware equipment cannot be loaded to withstand network needs, leaving hackers and viruses to break through the Internet, causing the leakage of network information or network paralysis. Therefore, the network security sentinel cannot be beaten at a moment.
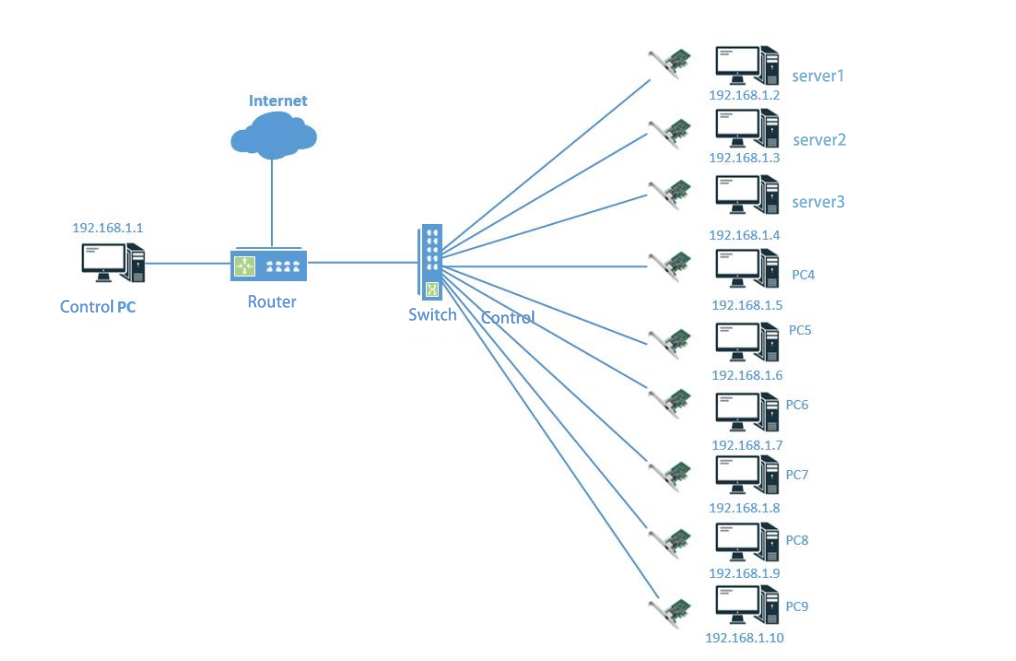
As a supplier of professional network card solutions, LR-LINK has 15 years of industry experience in the field of network card segmentation. Knowing that the hardware equipment is very important for network configuration and use, it has launched more than a hundred industry boutiques. Among them Intersection network cards (LREM3500PF-4SFP) and 10G dual-optical mouth BYPASS network card (product model: LRES1022pf-BP-SR) is favored by customers at home and abroad in the field of information security.

The hardware equipment in the field of network security is slightly different from other applications. It pays more attention to the customization needs of hardware and its own product specifications. The LR-LINK scattering network card uses 167.4mm*72mm standardized product size, from 1G to 40g, from dual-port to eight ports, from copper cables to optical fiber, complete product specifications, strong performance and stable performance. Both are adapted to running non -stop all -weather. When guarding your network security, it will not be stunned for a moment.
As a link for data transmission, the network card should be like a strong "sentinel". It has an open adaptation gallery and constructing integrated self -service capabilities to minimize the workload required to integrate with the network and support system integration. The safety and stability of transmission.
Cyber Security Guardian, please recognize the LR-Link brand!
